Update Cloud9 Configuration
Update Cloud9 configuration
Cloud9 will manage IAM credentials automatically. This default configuration is currently not compatible with EKS authentication via IAM, we will need to disable this feature and use the IAM Role.
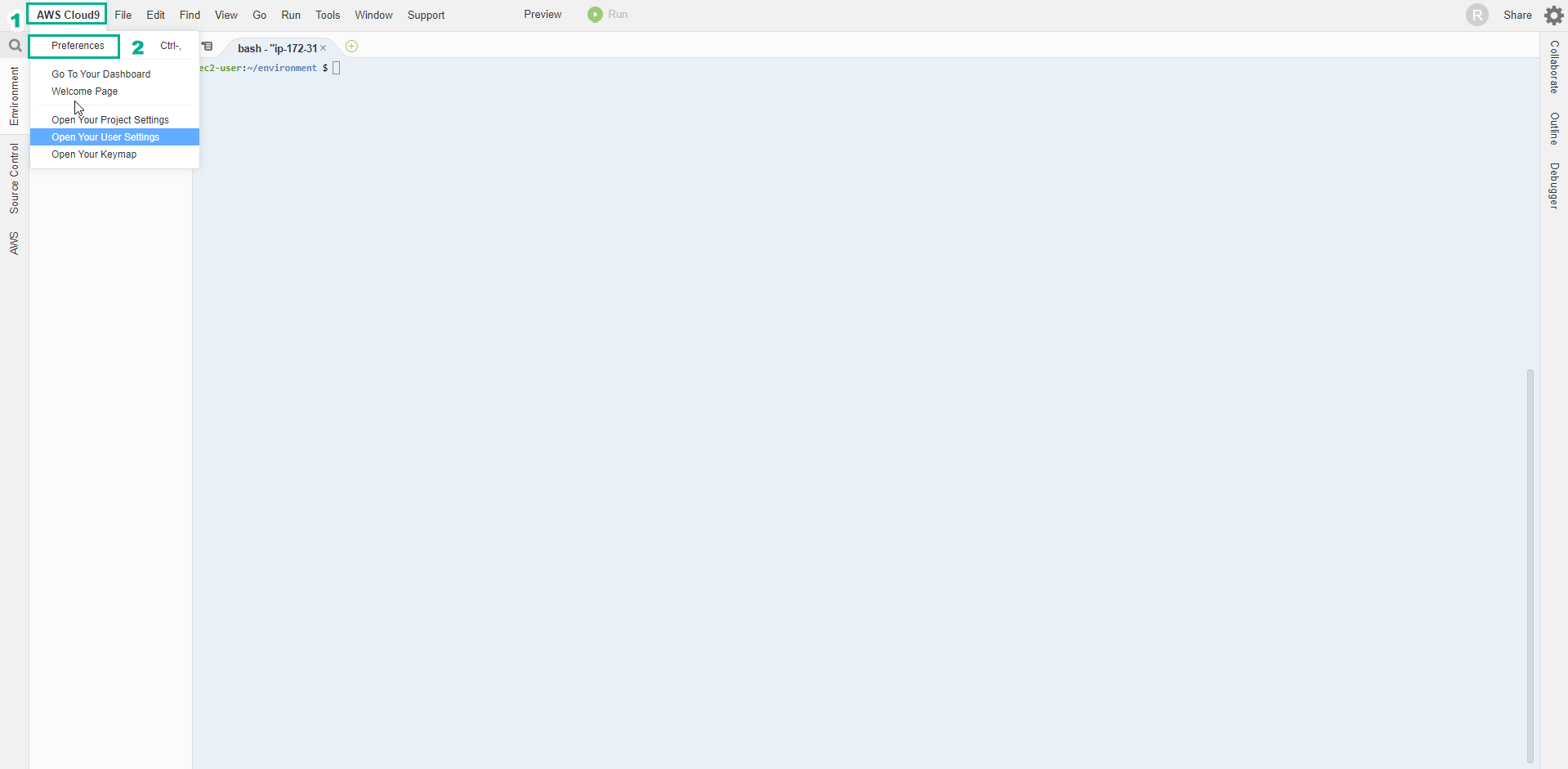
- In the AWS Cloud9 interface
- Select AWS Cloud9
- Select Preferences
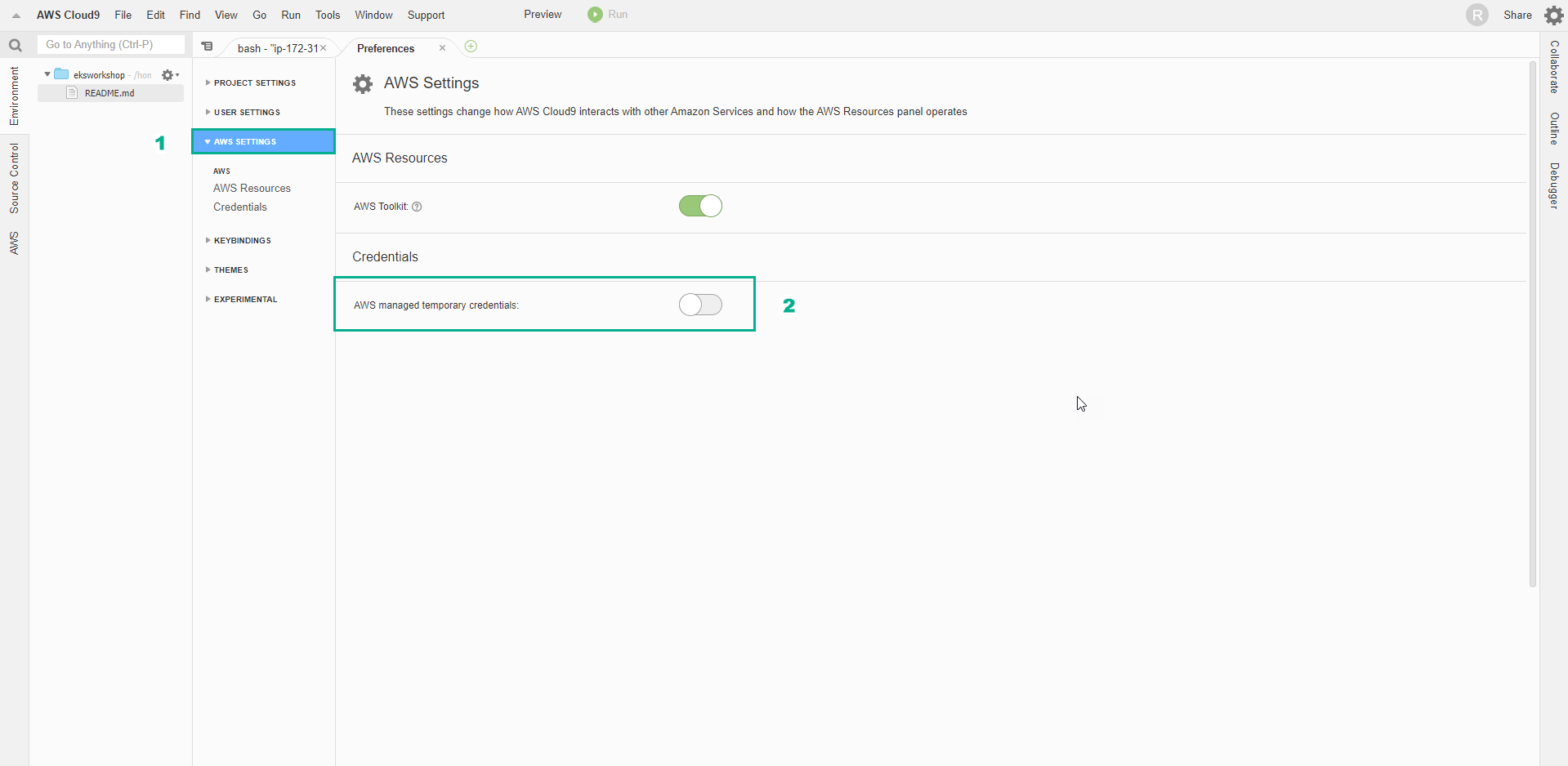
- In the AWS Cloud9 interface
- Select AWS SETTINGS
- Uncheck AWS managed temporary credentials
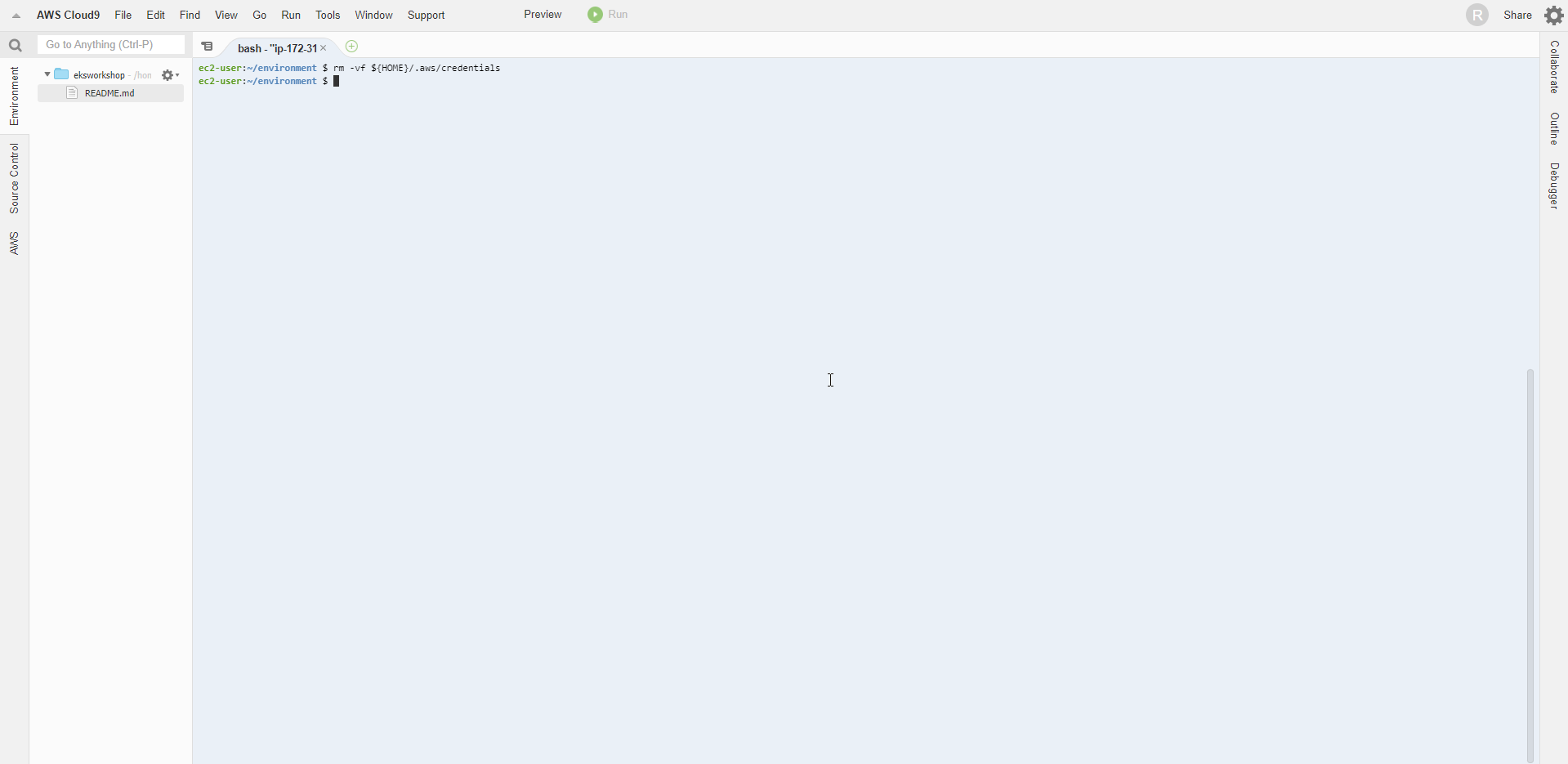
- To ensure that temporary credentials are not saved in Cloud9, we will delete all existing credentials with the command below.
rm -vf ${HOME}/.aws/credentials
- Next we will configure the aws cli to use the current Region.
export ACCOUNT_ID=$(aws sts get-caller-identity --output text --query Account)
export AWS_REGION=$(curl -s 169.254.169.254/latest/dynamic/instance-identity/document | jq -r '.region')
export AZS=($(aws ec2 describe-availability-zones --query 'AvailabilityZones[].ZoneName' --output text --region $AWS_REGION))
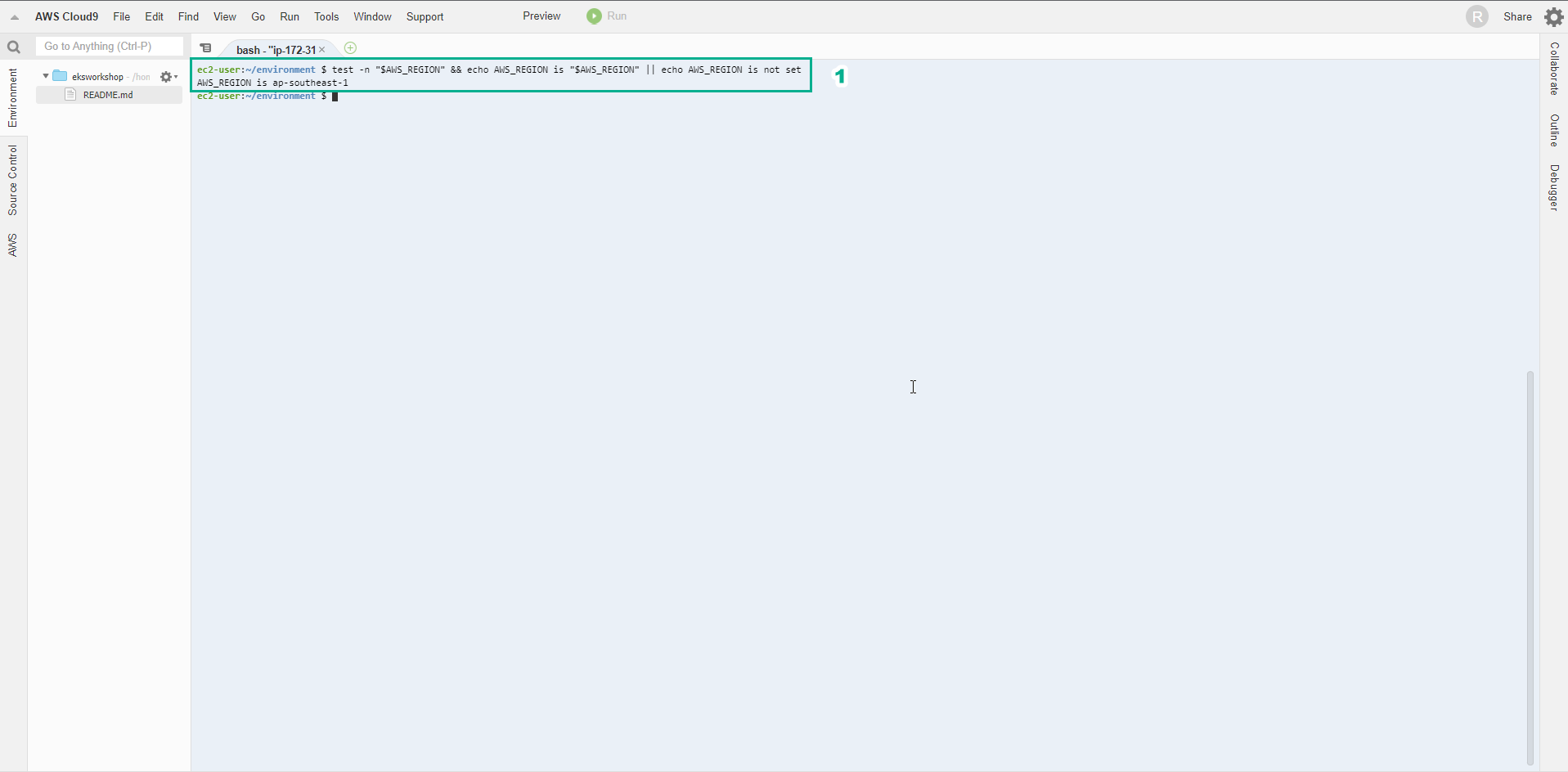
- Check that AWS_REGION has been set to the correct current Region.
test -n "$AWS_REGION" && echo AWS_REGION is "$AWS_REGION" || echo AWS_REGION is not set
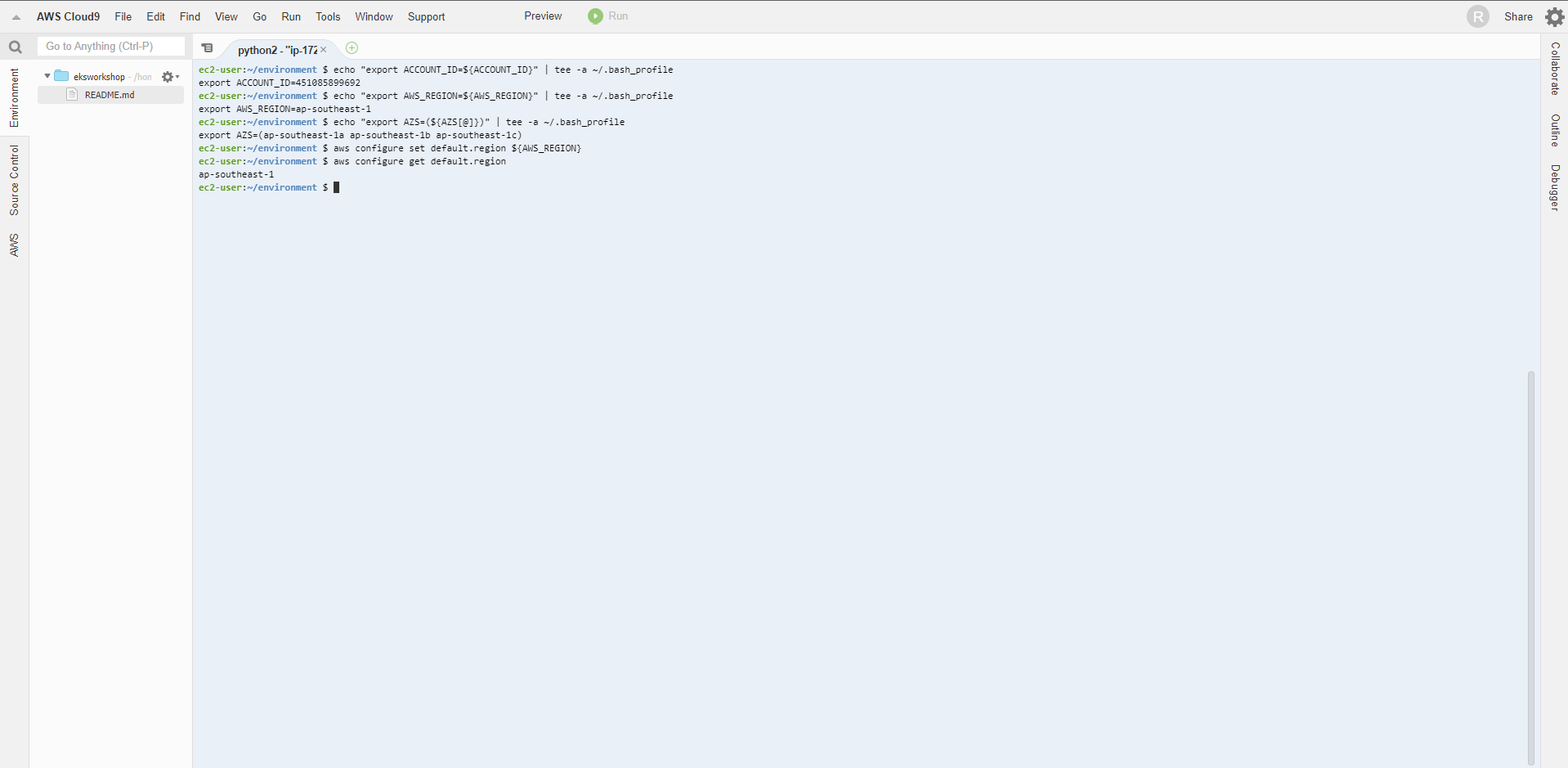
- Next we will save the configuration information to bash_profile
echo "export ACCOUNT_ID=${ACCOUNT_ID}" | tee -a ~/.bash_profile
echo "export AWS_REGION=${AWS_REGION}" | tee -a ~/.bash_profile
echo "export AZS=(${AZS[@]})" | tee -a ~/.bash_profile
aws configure set default.region ${AWS_REGION}
aws configure get default.region
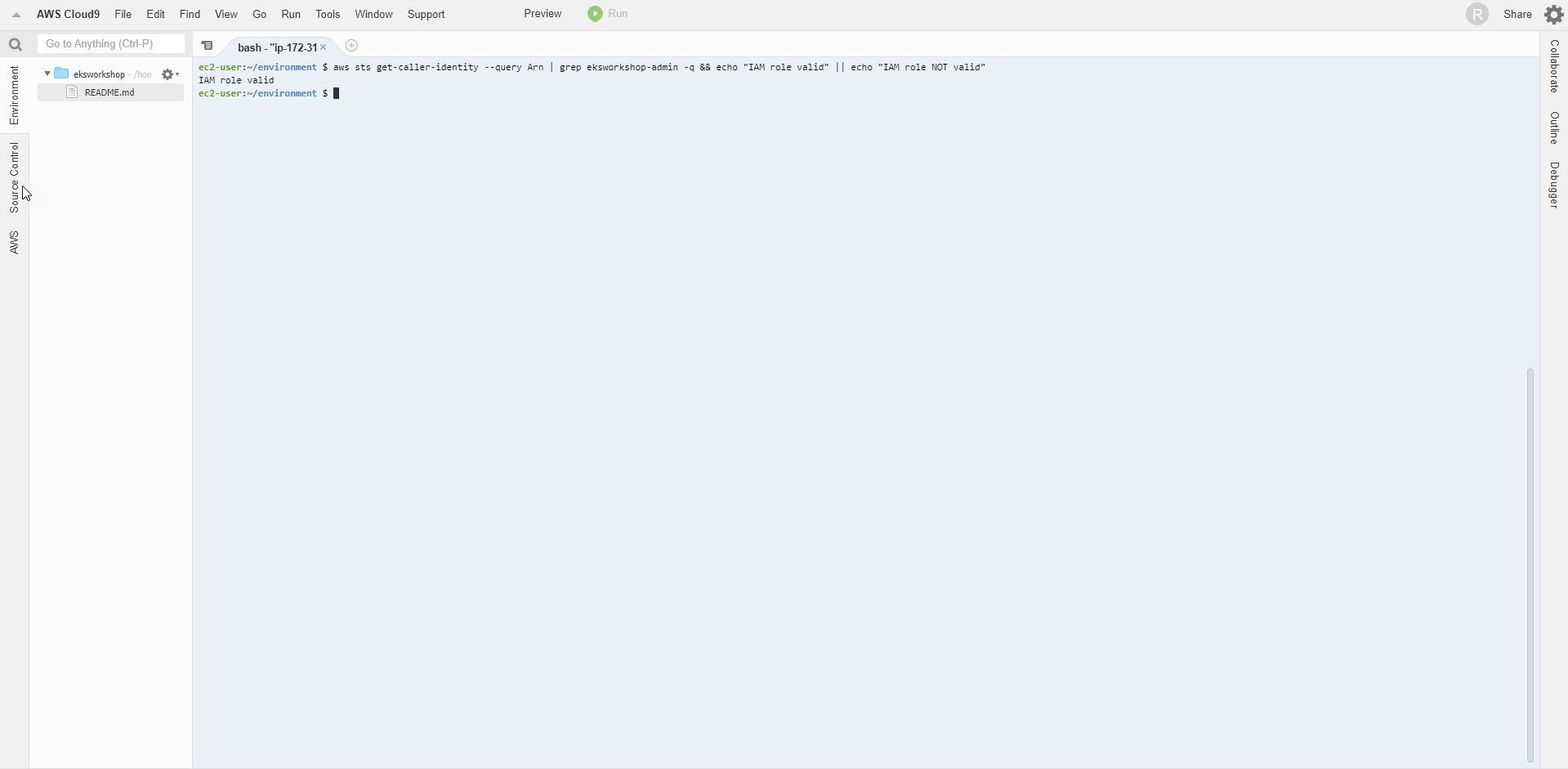
- Check IAM Role
- We will use the command to check if the Cloud9 IDE is using the IAM Role correctly.
aws sts get-caller-identity --query Arn | grep eksworkshop-admin -q && echo "IAM role valid" || echo "IAM role NOT valid"